News
Post by ATHENE researcher on APNIC Blog: Resurrection of injection attacks
In his blog post ATHENE researcher Philipp Jeitner, scientist at Fraunhofer SIT and TU Darmstadt, describes how the Domain Name System (DNS) can be exploited for injection attacks against a variety of different applications. He also shows why countermeasures aren't as easy as to apply patches to vulnerable implementations. A tool to test DNS resolver for vulnerabilities is also linked in the post.
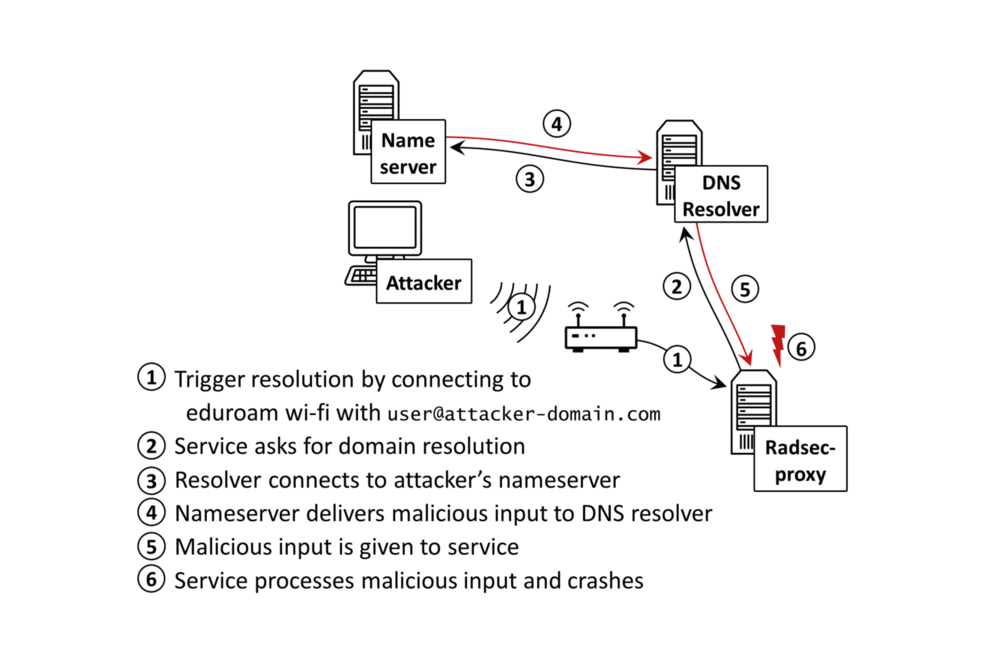
The article is based on the paper "Injection Attacks Reloaded: Tunnelling Malicious Payloads over DNS", written by Philipp Jeitner and Haya Shulman, which they presented at USENIX Security 2021.
Philipp Jeitner presented their work in a talk at NANOG 83 (link to the talk on YouTube) and in a Science Deep Dive Talk, also available on YouTube.
APNIC stands for Asia Pacific Network Information Centre and is a platform used by network operators and researchers for active exchange on current research topics.
show all news
