News
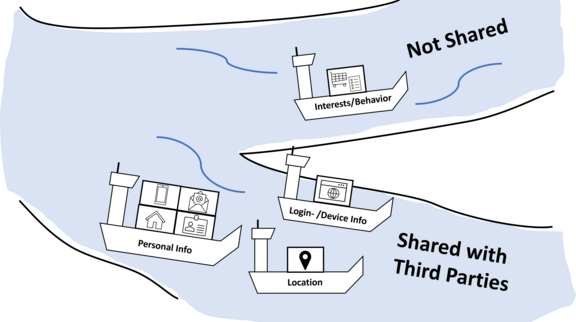
ATHENE Study shows: Visualizations help to better understand privacy statements
ATHENE researchers, in collaboration with ETH Zurich, have conducted a groundbreaking study on the visualization of privacy notices. The research was presented at the renowned IEEE Symposium on Security and Privacy (S&P) and demonstrates significant improvements in user understanding through image-based communication approaches.
read more
Prof. Dr. Iryna Gurevych receives first ATHENE Distinguished Professorship
Prof. Dr. Iryna Gurevych from the TU Darmstadt receives the first ATHENE Distinguished Professorship, recognizing her outstanding contributions to connecting artificial intelligence and cybersecurity. The award honors her internationally recognized research in computational linguistics and its innovative application to protect against manipulative language attacks and disinformation.
read more
Prof. Mira Mezini confirmed in the DFG Senate
The General Assembly of the German Research Foundation (DFG) elected Prof. Mira Mezini to the Senate of Germany's largest research funding organization for a second term of office at the DFG Annual Meeting in Hamburg. As a representative of TU Darmstadt on the ATHENE Board, she strengthens the representation of cybersecurity research in the central body of scientific self-administration.
read more
AirGuard extends protection with Google tracker - New research results on PETS 2025
The AirGuard-App for Android and iOS was developed a few years ago and offers protection against potential stalking. It scans the environment to detect trackers such as AirTags, SmartTags or other trackers and informs users of the potential danger of being followed. The app has now been expanded to include protection functions against the new Google trackers and has reached the milestone of 1.5 million downloads worldwide thanks to continuous further development.
read more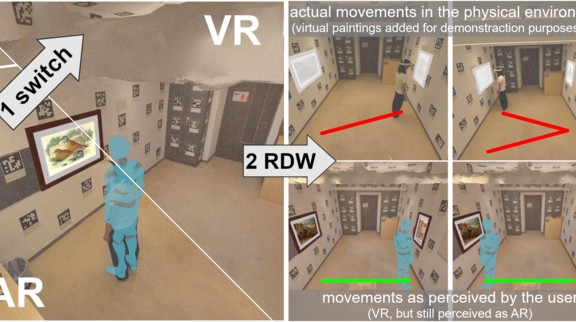
ATHENE research on perception manipulation in augmented reality honored at CHI 2025
ATHENE researchers presented their innovative research on “SwitchAR” at the renowned CHI Conference 2025 in Yokohama and received the Jury Honorable Mention Award. The technology, developed as part of the ATHENE project “XR-Guard - A Security Mechanism to Detect and Mitigate Perceptual Manipulations in Extended Reality” under the coordination of Prof. Jan Gugenheimer, enables the application of perceptual manipulations in augmented reality (AR) environments for the first time.
read more